OSI MODEL
1. THE OSI MODEL WAS DEVELOPED BY THE INTERNATIONAL ORGANIZATION FOR STANDARDIZATION (ISO) IN THE LATE 1970S. THE MAIN ARCHITECT OF THE OSI MODEL WAS HUBERT ZIMMERMANN, A FRENCH SOFTWARE ENGINEER.
2. HIS MODEL REPRESENT A 7 LAYER
3. OSI MEANS (OPEN SYSTEMS INTERCOMMUNICATIO).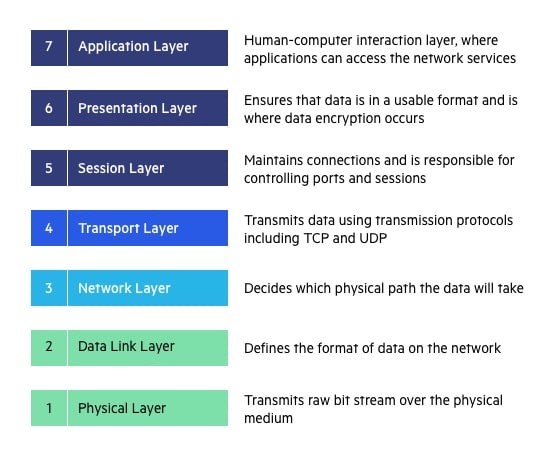
1. APPLICATION LAYER
1. THE APPLICATION LAYER IS USED BY END-USER SOFTWARE SUCH AS WEB BROWSERS AND EMAIL CLIENTS.
IT PROVIDES PROTOCOLS THAT
ALLOW SOFTWARE TO SEND AND RECEIVE INFORMATION AND PRESENT MEANINGFUL DATA TO
USERS.
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE APPLICATION LAYER.
WHICH IN TURN WORKS AT THE APPLICATION LAYER.MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
FTP (FILE TRANSOFER PROTOCOL)
DNS (DOMAIN NAME SYSTEM)
HTTP (HYPER TEXT TRANSFOR PROTOCOL)
DEVICES
ALL END DEVICES USED IN LAYER.
___________
2. PRESENTATION LAYER
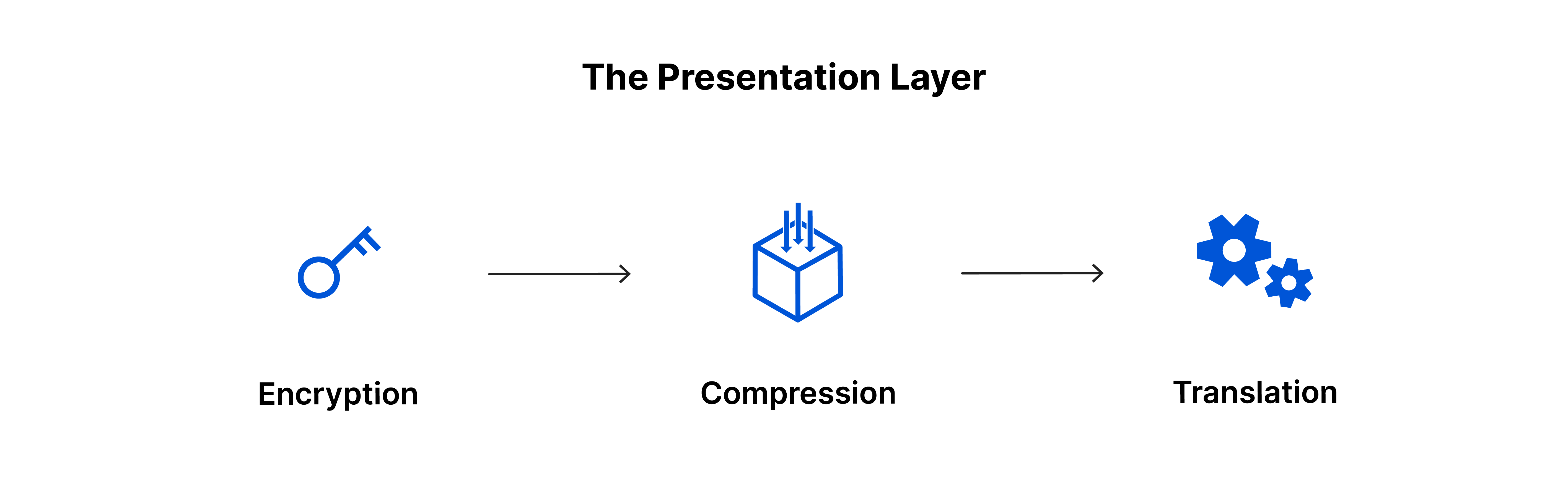
1. THE PRESENTATION LAYER RECEIVED THE DATA FROM APPLICATION LAYER AND PROCESSES THE RAW DATA AND THEN COMPRESSES THE DATA AND ENCODE THE DATA SO SESSION LAYER EASILY RECIEVE THE DATA.
2. PRESENTATION LATER SENDS ITS DATA IN PDU FORMAT.
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE PRESENTATION LAYER.
WHICH IN TURN WORKS AT THE PRESENTATION LAYER.MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
NCP (NETWARE CORE PROTOCOL)
LPP (LINEAR PROGRAMMING PROBLEM)
DEVICES
GATEWAY OR FIREWALL OR PC.
______________
3. SESSION LAYER
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE SESSION LAYER.
WHICH IN TURN WORKS AT THE SESSION LAYER.MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
PPTP (POINT-TO-POINT TUNNLING PROTOCOL)
RPC (REMOTE PROCRDURE CAL PROTOCOL)
SCP (SESSION CONTROLL PROTOCOL)
DEVICES
GATEWAY OR FIREWALL OR PC.
___________
4. TRANSPORT LAYER
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE TRANSPORT LAYER.
WHICH IN TURN WORKS AT THE TRANSPORT LAYER.MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
TCP (TRANSMISSION CONTROLL PROTOCL)
UDP (USER DATAGROUND PROTOCOL)
DEVICES
GATEWAY OR FIREWALL PC.
_________________
5. NETWORK LAYER
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE NETWORK LAYER.
WHICH IN TURN WORKS AT THE NETWORK LAYER.MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
IPV4 (INTERNET PROTOCOL VERSION 4)
IPV6 (INTERNET PROTOCOL VERSION 6)
ICMP (INTENET CONTROLLL MESSAGE PRTOCOL)
DEVICES
ROUTER.
MULTY LAYER SWITCH.
_________________
6. DATA LINK LAYER
THE DATA LINK LAYER BREAKS DATA UP INTO SMALLER UNITS CALLED
FRAMES.
IT ADDS ERROR-CHECKING INFORMATION TO EACH FRAME.
IT TRANSMITS THE FRAMES ACROSS THE PHYSICAL LAYER.
IT HANDLES FLOW CONTROL, WHICH ENSURES THAT THE SENDER DOES NOT
SEND DATA FASTER THAN THE RECEIVER CAN RECEIVE IT.
IN OTHER WORDS, THE DATA LINK LAYER IS RESPONSIBLE FOR ENSURING THE RELIABLE DELIVERY OF DATA BETWEEN TWO NODES ON A NETWORK. IT DOES THIS BY ADDING ERROR-CHECKING INFORMATION TO EACH FRAME, AND BY RETRANSMITTING FRAMES THAT ARE CORRUPTED OR LOST. THE DATA LINK LAYER ALSO HANDLES FLOW CONTROL, WHICH ENSURES THAT THE SENDER DOES NOT OVERWHELM THE RECEIVER.
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE DATA LINK LAYER.
WHICH IN TURN WORKS AT THE DATA LINK LAYER .MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
(PPP) Point To Point Protocol.
(LCP) Link Control Protocol
(LAP) Link Access
Procedure.
(NCP ) Network Control Protocol .
DEVICES
NIC
WIRELESS ACCESS POINT
ETHERNET SWITCH.
________________
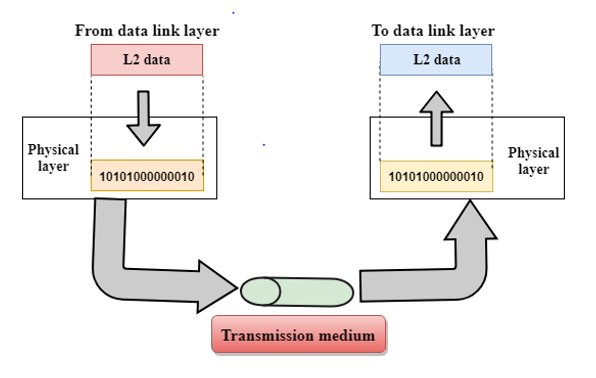
7.PHYSICAL LAYER
THE PHYSICAL LAYER TRANSMITS AND RECEIVES DATA BITS OVER A
COMMUNICATION CHANNEL.
IT DOES THIS BY ENCODING THE DATA BITS INTO A PHYSICAL SIGNAL,
SUCH AS A VOLTAGE LEVEL OR LIGHT PULSE.
IT ALSO ENSURES THAT THE DATA BITS ARE TRANSMITTED AND RECEIVED IN
A SYNCHRONIZED MANNER.
THE PHYSICAL LAYER MAY ALSO BE RESPONSIBLE FOR DETECTING AND
CORRECTING ERRORS IN THE DATA BITS THAT ARE TRANSMITTED.
IN OTHER WORDS, THE PHYSICAL LAYER IS RESPONSIBLE FOR THE PHYSICAL
ASPECTS OF DATA TRANSMISSION, SUCH AS THE TYPE OF SIGNAL USED, THE SPEED OF TRANSMISSION,
AND THE ERROR DETECTION AND CORRECTION MECHANISMS.
THERE ARE SOME PROTOCOLS THAT WORK AT THE BACKEND OF THE PHYSICAL LAYER.
WHICH IN TURN WORKS AT THE DATA LINK LAYER .MANY DEVICES USE IT AT THE APPLICATION LAYER.
PROTOCOLS
1. ETHERNET
2. BLUETOOTH.
3. DSL
4. WIFI
DEVICES
CABLE
CONNECTOR
NETWORK INTERFACE CARD
______________________
|
OSI Layer |
PDU Name |
Key Header Information |
|
Application |
Data |
User data, no header added here. |
|
Presentation |
Data |
Data is formatted, compressed, or encrypted. |
|
Session |
Data |
Manages session state, no new header added. |
|
Transport |
Segment |
Source/Destination ports, Sequence number, Acknowledgment, etc. |
|
Network |
Packet |
Source/Destination IP, TTL, Protocol, Header checksum. |
|
Data Link |
Frame |
MAC addresses, Type, FCS for error checking. |
|
Physical |
Bits |
0s and 1s for transmission as electrical/radio/optical signals. |
IF YOU WANT PDF IN URDU TRANSLATION OF THIS BLOG THEN CLICK ON "ABDUL MANAN JAVED"
 |
| Pop Out |
BELOW AFTER CLICKING, A WINDOW WILL OPEN BELOW AND WHAT IS SHOWN IN THE IMAGE IS TO CLICK ON THE POP-OUT AND YOU WILL HAVE A PDF OPEN AND YOU CAN ALSO DOWNLOAD IT.



Comments
Post a Comment