WHAT IS INTRUDER
1. HE IS JUST A PERSON WHO IS TRYING TO GAIN UNAUTHORISED ACCESS TO A SYSTEM ON NETWORK WITH CRIMINAL INTENTION.
IT CAN COMPLETELY CONTROL AND TERMINATE AND CRUPTE THIS NETWORK.
TYPES OF INTRUDER
1. INSIDE INTRUDER
2. OUTSIDE INTRUDER
OUTSIDE INTRUDER
HE IS ACTUALLY NOT HAVING AREA AUTHORISED ACCESS TO THE SYSTEM OR NETWORK.
INSIDE INTRUDER
1. HE IS HAVING SOME AUTHORISED ACCESS TO THE SYSTEM OR NETWORK BUT IS SOME RESTRICTIONS. HE DO NOT USE IS FOR THE PURPOSE OF SYSTEM.
2. INSIDE INTUDOR IS HARMFUL THAN THE OUTSIDE INTRUDER BECAUSE VERY DIFFICULT TO IDENTIFY HIS.
WHAT IS IPS
1. IN SHORT, AN INTRUSION PREVENTION SYSTEM (IPS), ALSO KNOWN AS INTRUSION DETECTION PREVENTION SYSTEM (IDPS),
2. IPS IS A NETWORK SECURITY TOOL WHICH CAN BE HARDWARE OR SOFTWARE THAT CONTINUOUSLY MONITORS ARE NETWORK FOR MALICIOUS ACTIVITY AND TAKES ACTION TO PREVENT IT.
IT INCLUDING REPORTING BLOCKING OR DROPPING IT. WHEN IT DOES OCCUR.
___________
WHO IS WORK IPS
1. HOW AN IPS WORKS. AN INTRUSION PREVENTION SYSTEM WORKS BY ACTIVELY SCANNING FORWARDED NETWORK TRAFFIC FOR MALICIOUS ACTIVITIES AND KNOWN ATTACK PATTERNS.
2. THE IPS ENGINE ANALYZES NETWORK TRAFFIC AND CONTINUOUSLY COMPARES THE BITSTREAM WITH ITS INTERNAL SIGNATURE DATABASE FOR KNOWN ATTACK PATTERNS.
___________
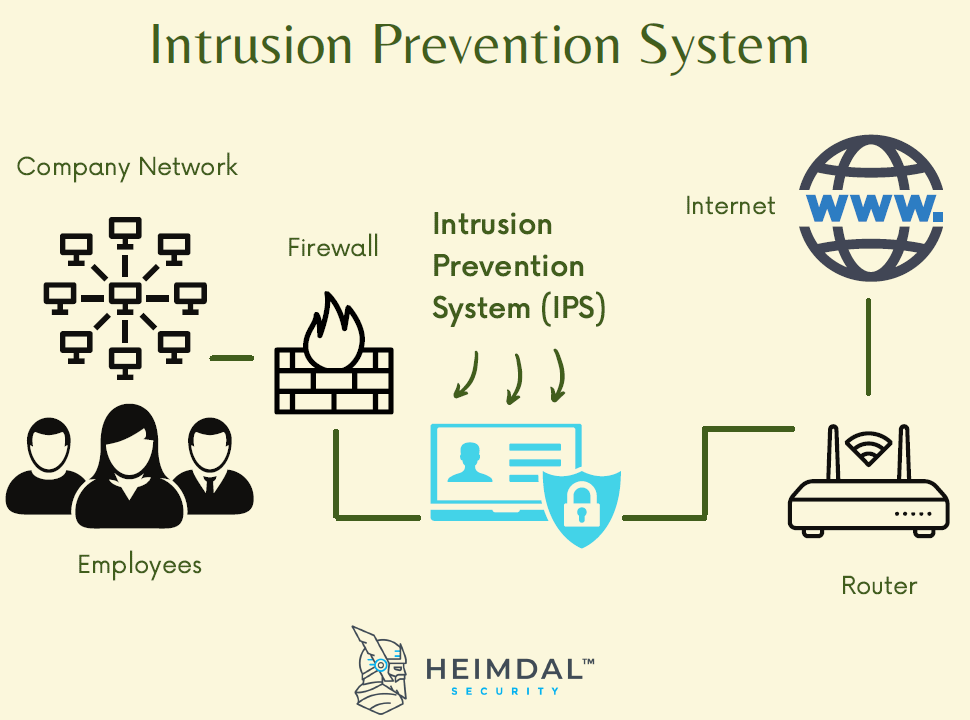 |
| FIGURE OF IPS |
TYPES OF IPS
1. (NIPS) NETWORK-BASED INTRUSION PREVENTION SYSTEM . A NIPS MONITORS AND PROTECTS AN ENTIRE NETWORK FROM ANOMALOUS OR SUSPICIOUS BEHAVIOR.
2. (WIPS) WIRELESS INTRUSION PREVENTION SYSTEM.
3. (HIPS) HOST-BASED INTRUSION PREVENTION SYSTEM.
__________
IP IPS STANDS FOR INTRUSION PREVENTION
SYSTEM (IPS). IT IS A NETWORK SECURITY DEVICE THAT MONITORS NETWORK TRAFFIC FOR
MALICIOUS ACTIVITY AND TAKES ACTION TO BLOCK OR PREVENT IT.
IPS CAN BE USED TO PROTECT
AGAINST A WIDE RANGE OF THREATS, INCLUDING:
VIRUSES
WORMS
TROJANS
SPYWARE
DENIAL-OF-SERVICE ATTACKS
PORT SCANS
ZERO-DAY ATTACKS
IPS WORKS BY INSPECTING NETWORK TRAFFIC FOR
PATTERNS THAT MATCH KNOWN ATTACK SIGNATURES. IF A MATCH IS FOUND, THE IPS CAN
TAKE ACTION TO BLOCK OR PREVENT THE ATTACK,
SUCH AS:
DROPPING THE PACKET
LOGGING THE PACKET
SENDING AN ALERT
TAKING CONTROL OF THE INFECTED SYSTEM.
IPS CAN BE DEPLOYED IN A
VARIETY OF WAYS, INCLUDING:
AS A STANDALONE DEVICE
AS A MODULE IN A FIREWALL OR ROUTER
AS A VIRTUAL APPLIANCE
IPS IS AN IMPORTANT PART OF A COMPREHENSIVE
NETWORK SECURITY STRATEGY. BY DETECTING AND PREVENTING MALICIOUS ACTIVITY, IPS
CAN HELP TO PROTECT NETWORKS FROM A WIDE RANGE OF THREATS.
HERE ARE SOME OF THE
BENEFITS OF USING AN IP IPS:
IT CAN HELP TO PREVENT CYBERATTACKS.
IT CAN HELP TO IDENTIFY AND RESPOND TO
SECURITY THREATS.
IT CAN HELP TO IMPROVE NETWORK PERFORMANCE.
IT CAN HELP TO REDUCE THE RISK OF DATA
BREACHES.
____________
DIFFREENCE BETWEEN IDS AND IPS

Comments
Post a Comment