Twisted-Pair Cable
1. Twisted-Pair Cables Were Among The Earliest
Guided Transmission Media, Along With Coaxial Cables.
2. Today, Twisted Pair Cables Are Used In Many
Applications In Networking And Communications, For Example, In Telephone Lines,
Digital Subscriber Lines And Local Area Networks.
Benefits Or Advantages Of Twisted Pair Cable
1. It Is The Most Expensive Means Of Delivery For
Short Distances.
2. It Is Relatively Easy To Implement And
Eliminate.
3. It Can Be Used To Carry Both Analog And Digital
Data.
TYPES OF CABLE
1. SHIELD TWISTED-PAIR CABLE. (STP).
2. UNSHIELD TWISTRD-PAIR CABLE. (UTP).
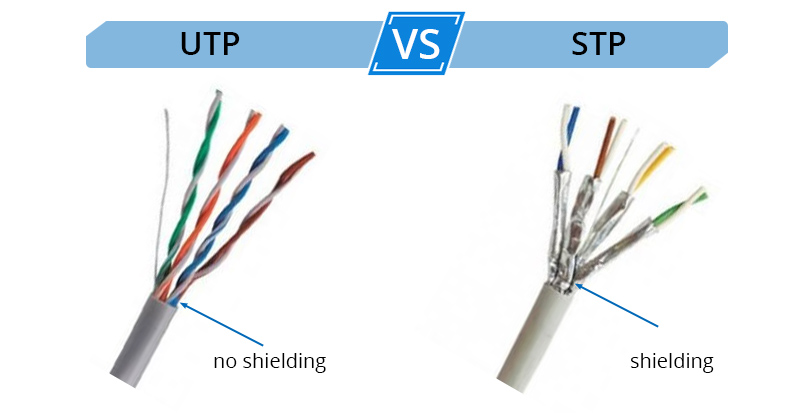
STP CABLE
Shielded Twisted Pair (Stp) Is A Special Kind Of Copper Telephone And Local Area Network (Lan) Wiring Used In Some Business Installations.
UTP CABLE
UTP Cables Are Used As Ethernet Cables And Telephone Wires For Short To Medium Distances To Transfer Data And Audio Signals.
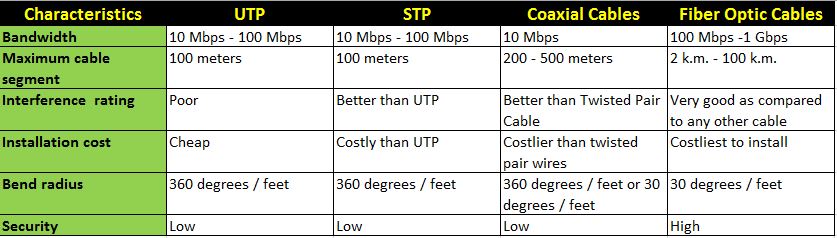
DIFFERENCE BETWEEN STP AND UDP
 |
| Diagram View |
 |
| Details View |
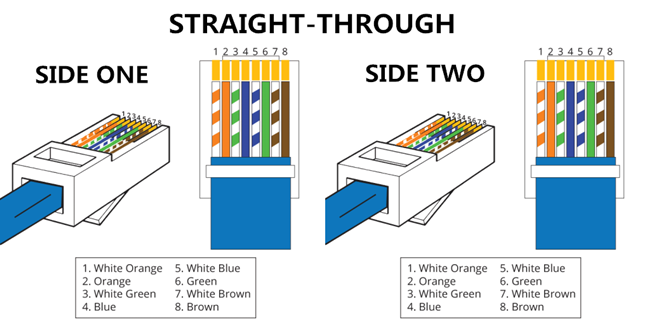
STRAIGHT CABLE
Connect Different Devices Together.
A Crossover Cable Is When Both End Of A Cable Are Wired Using The Same Standerd.
Colour Coding : White Orange , Orange . White Green , Blue . White Blue , Green . White brown , Brown.
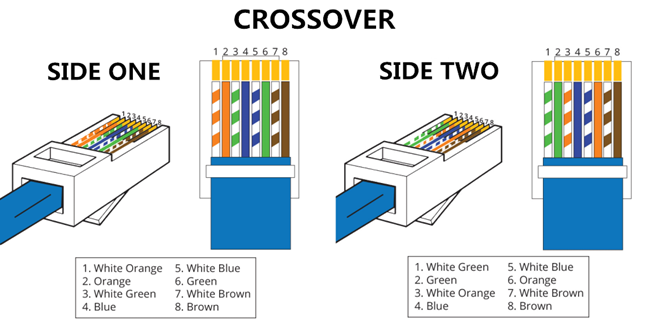
CROSSOVER CABLE
Connects The Same Devices Together.
A Crossover Cable Is When Both End Of A Cable Are Wired Using The Two Different Standerds. One Is 568A And Second Is 568B.
Colour Coding : White Green, Green . White Orange , Blue . White Blue , Orange . White Brown , Brown
RJ 45 CONNECTOR TYPES COLOURE CODE
____________
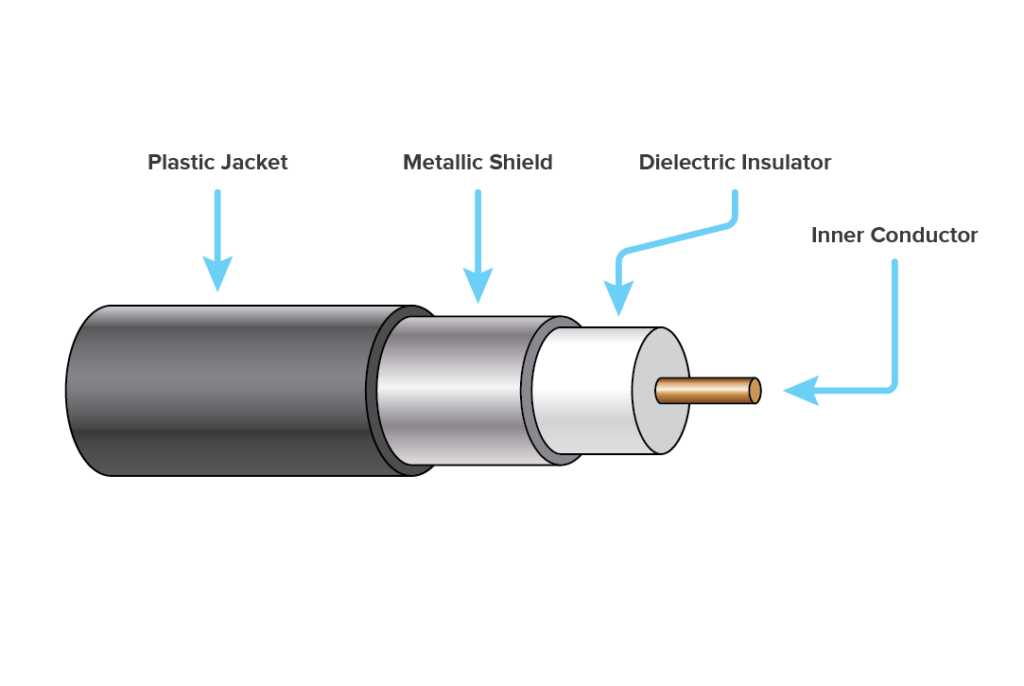
COAXIAL CABLE
Coaxial Cable Supports High-Speed Signal
Transmission Over Greater Distances Than Other Cables Such As Twisted Pair
Cables.
5 Unique Benefits Of Coaxial Cable
1. Coax Supports Higher Bandwidth Levels.
2. Coax Is Easy To Install.
3. Cox Is Easy To Find.
4. Coax Can Provide Power.
5. It Is Uneven.
 |
| Connector Coaxial Cable |
 |
| Image Coaxial Cable |
_____________
Fiber Optics Cable
1. Fiber Optic Internet, Commonly Referred To As
Fiber Internet Or Simply "Fiber," Is A Broadband Connection That Can
Reach Speeds Of Up To 940 Megabits Per Second With Low Latency.
2. Fiber Optics Is Used For Long-Distance And
High-Performance Data Networking. It Is Also Commonly Used In Telecommunication
Services, Such As The Internet, Television, And Telephone
3. Better Bandwidth. Fiber Optic Cables Have Much
Higher Bandwidth Than Metallic Cables.
BENIFITS OF HIS CABLE
1. More
Bandwidth Means Faster Speeds.
2. Long
Transmission Distance.
3. More
Flexibility.
4. Better Latency.
5. Strong Security.
____________








Comments
Post a Comment